Cyber threats change regularly. Fraudsters implement new tactics to expose vulnerabilities and gain access to devices or networks.
Cybercriminals have different motives to target a specific person or organization. Some of the most common motives include sabotage, retaliation, financial gain, surveillance and information exposure.
Statista states global email usage will grow to more than 4.7 billion users in 2026. Given how popular emails are, it shouldn’t surprise that they present a perfect opportunity for fraudsters to strike.
Email security ought to be part of cyber hygiene. Let’s look at email security and how to create a strategy to minimize email security threats.
What is Email Security?
Email security can be defined as creating a set of techniques to protect email communications. The strategy’s goal is to preserve:
- Email message confidentiality;
- Email message integrity;
- Email message availability.
How Secure is Email?
Dr. Catherine Ullman, senior information security analyst at the University of Buffalo, suggests that emails are not secure for sharing information.
The communication method was never intended for sensitive data. You need login credentials to access the inbox, but it’s hardly sufficient when you consider human error factors.
Some users dismiss potential threats and stick to simple and easy-to-crack passwords. Others are gullible enough to fall for phishing scams.
In a way, it’s like having a fancy lock on your door but leaving the key under the doormat. If the culprit knows where to look for a key due to the carelessness of the homeowner, they will not have trouble getting in.
On the other hand, if the homeowner is smart and takes the necessary precautions, they can rest easier knowing they are safe.
Exactly for this reason, we have written an article on how to send a secure email.
Why is Email Security Important?
Despite cybersecurity threats, emails remain among the most popular communication channels. Individuals or organizations will not abandon the method despite the fact that over 90% of attacks on organizations start from a malicious email.
Instead, they should look to enforce email security in tandem with general data protection regulation practices.
Email security has multiple benefits, such as:
- Real-time protection against zero-day exploits;
- Data breach prevention;
- Improved confidentiality;
- Protection from phishing attacks and spoofing;
- Identification of malicious threats and spam emails;
- Compromised account takeover and identity theft prevention.
Email security shouldn’t be just a measure to protect individual inboxes. For organizations, it’s a practice to avoid financial loss and other dangers.
How Does Encryption Protect Email?
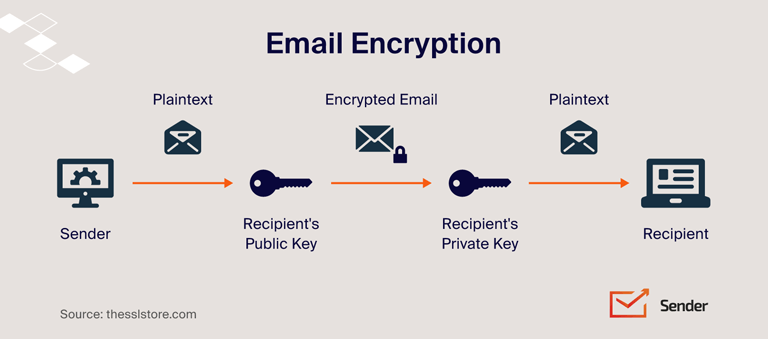
As mentioned, most email service providers offer encryption as a security measure. It’s an authentication process that blocks unauthorized access to view the contents.
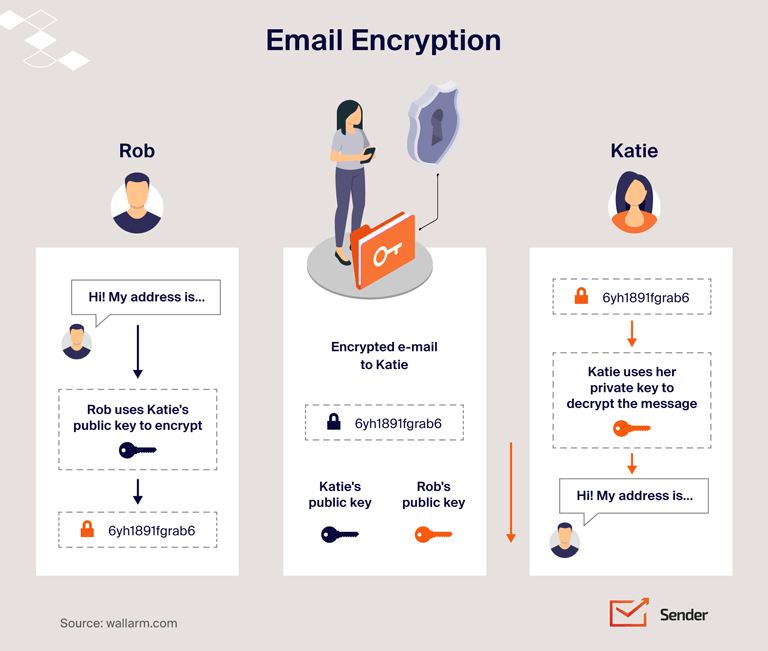
Encryption scrambles the message and makes it unreadable for third parties trying to access the information. Only the recipient who has the private key can decode the message.
Basic email encryptions no longer require computer systems. Contemporary email encryption software comes in a cloud-based service. Or, as an alternative, organizations host the solution privately.
There are three major email encryption types:
1. TLS. TLS stands for Transport Layer Security. TLS uses a special code to jumble up the messages while they’re on the move. It’s like putting your message in an envelope, sealing it, and then adding a secret lock. Only the intended recipient has the means to unlock and read the message.
2. S/MIME. S/MIME is your standard email encryption type to offer a secure email gateway via encryption and digital signatures. It’s like going to a post office and signing off on a package before you can receive and unpack it.
3. PGP. PGP (Pretty Good Privacy) is similar to S/MIME but doesn’t require a deciphering key directly from a particular certificate authority. Using the same post office example, it’s like taking a package without interacting with a post office worker. Instead, you go to a dedicated pickup point and enter a code you received beforehand.
Types of Email Attacks
Understanding the basics of email attack types can be enough to help organizations protect themselves. Below is a list of the most common email attacks.
- Spam. Spam, also known as unsolicited email, pushes advertisements and other calls to action to persuade recipients to open an email. Spammers want to obtain sensitive data. They try to trick people into clicking on harmful links that redirect to malware-infested landing pages;
- Identity theft. Attackers target email accounts to steal data related to an individual’s personal information. Credit card numbers, social security numbers, home addresses, etc., help criminals carry out fraudulent activities;
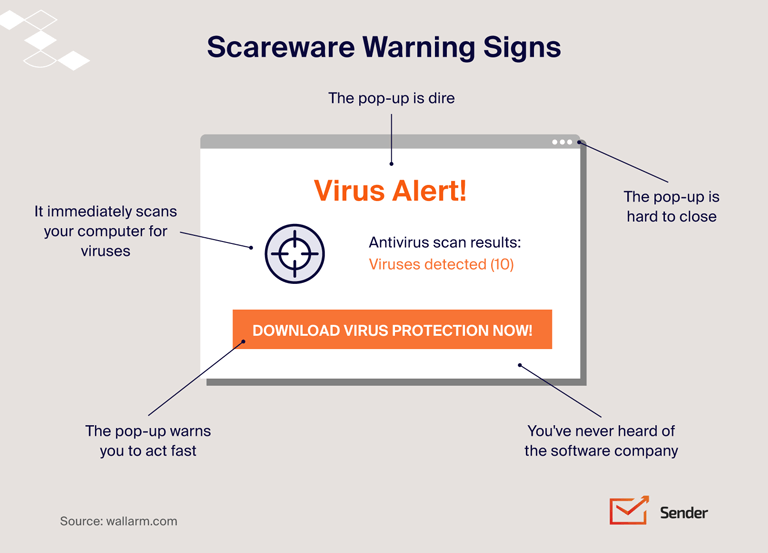
- Scareware. Scareware creates pop-ups to create a Windows-like message telling that something is wrong with the computer’s operating system. The prompt suggests downloading and installing the indicated software is the only solution. Unsuspecting users take action and spread malware;
- Phishing. Malicious actors impersonate reputable individuals and try to gather information for personal gain, like login credentials or credit card numbers. Phishing tends to be personalized and takes longer as fraudsters take their time to paint themselves as trustworthy. It’s the most common form of cybercrime, with about 3.4 billion spam emails sent daily. Once the unsuspecting user falls for the trick, a phisher asks for a specific action, such as sharing the information directly or giving login credentials;
- Vishing. Voice communication technology is advanced enough to pose a threat to unsuspecting individuals. Vishing is a form of phishing campaigns that utilizes voice. Criminals record voice messages and send them to specific recipients, often imitating authorities or bank employees;
- Ransomware. Criminals persuade recipients to install malicious software on devices and hold these devices hostage for ransom.
- Spoofing. Spoofers try to scam unsuspecting people by impersonating legitimate domains. Closer inspections usually reveal that the source is fake. For instance, instead of support@ahrefs.com, the domain is support@ahreffs.com. Alternatively, email spoofing involves using a real name and surname but a slightly modified domain.
Dangers of Malicious Emails
An organization’s network can be vulnerable enough that a single device might affect the entire enterprise. On the other hand, comprehensive protection strategies identify and flag a threat before it manifests.
Different email attacks exist for different reasons, but the overall dangers of malicious emails can be classified into a few major categories:
- Jeopardizing the organization’s assets. Malicious links or malicious code disrupt individual devices or entire systems, jeopardizing operations and causing delays.
- Data theft. Many email attacks have the purpose of stealing sensitive data. Falling for such malicious emails could be a human error, lack of experience, and failure to identify a threat.
- Ruining the organization’s reputation. Whether it’s phishing attacks or malicious software, external parties that gain unauthorized access to an email account do so because they have malicious intent. One of the intentions is to ruin an organization’s reputation. If the word gets out that fraudsters had an easy time gaining sensitive information, it will not take too long before the reputation hits rock bottom. Recovering from a customer data leak, for example, is a massive challenge.
How are Email Attachments Used in Attacks?
Email security solutions must consider how email attachments steal sensitive data and pose other threats.
Virtually any file type can be attached to an email. The file size is one of the restrictions, but it’s hardly a limitation to what a hacker can accomplish.
Common malicious email attachments to look out for include:
- Disk images. Files that end with .iso, .dmg, and .img infect the device after activation by the recipient, stealing login credentials;
- Archived files. .zip, 7z, and .rar files allow cyber attackers to archive malware and make it less obvious. An archived file conceals a threat, and hackers can name it to something innocent like “images” to fool the recipient;
- Executables. The .exe file extension screams that the attachment is dangerous. Still, people fall for it and download the file. From there, the executable runs codes and modifies the device’s system. The modifications range from file encryption to sensitive information exposure.
As a rule of thumb, recipients should block malicious emails if they come with suspicious attachments. If the sender’s email address is unfamiliar, it’s recommended to ignore any attachments.
Phishing emails often include attachments, too. In addition to tricking recipients, phishers develop advanced threats with the help of complementary files, i.e., email attachments.
Email Security Strategies
Organizations should integrate company-wide email security solutions and develop strategies that minimize potential risks.
Security awareness training is a solid foundation. The more people become aware of looming threats, the more they will pay attention to them. Not to mention that it’s easier to identify a risk once you know what to expect.
Utilizing modern solutions is another piece of good advice. Dedicated email security software can be the difference-maker between an organization dealing with data breaches constantly and an organization that automates security and can focus on other areas.
Finally, dedicated security teams with members who have defined roles also assist in fending off cyber attackers and developing modern security measures for email users.
Email Security Best Practices
Now that you know what general email security practices look like company-wide, consider how to apply the said strategies in practice on a more individual basis.
2FA Authentication
Don’t rely just on your password as a login credential. Implement multifactor authentication as an additional security layer to access your email account.
A second code, such as a text message to your phone or a biometric solution like facial recognition, complicates things for criminals.
Public Wi-Fi
Connecting to public Wi-Fi is inevitable when traveling or without access to cellular data or a dedicated home/work network.
The problem with the public internet is that it’s hardly a bastion of security. More often than not, it misses the necessary security protocols. Connecting to an unprotected Wi-Fi exposes your device.
If you have no choice but to use public Wi-Fi, make sure that you enable a virtual private network to encrypt the information exchange.
Spam and Unwanted Senders
If your email service provider fails to identify incoming spam, you must do it manually. Filter the recipient list by blocking spammers.
Pro tip: you can look for an ESP that excels in providing spam filters. Or, you can install a browser extension that offers the same.
Data Backup
Eliminating the risks completely is more or less impossible. Hence, supplemental backups and other backup options must exist within an organization.
An email attack may corrupt data, and there’s no telling how malicious the threat is. It’s better to be safe and sorry, which is what data backup offers.
Multiple Inboxes
Juggling multiple email inboxes is expected because you usually have personal and work inboxes. To make things easier, some people try to keep everything in a single inbox.
Such practice is not recommended. Imagine an employee who uses a work inbox to sign up for a service and submit data to a third party. They could use a separate inbox for personal needs.
Shady Websites
Some email attacks have a pattern of promoting specific websites, encouraging recipients to click on a URL and go to the landing page.
If such a thing occurs regularly, why not block websites on the device? Particularly if there’s another person using the same computer and isn’t yet aware of a threat from a website.
Learning how to block a website on Mac laptops and other devices isn’t that difficult. And you can always update the list to keep malicious websites out of sight.
Wrapping Up
Robust email security measures should not be taken lightly. Whether it’s a large organization or an individual, there’s a plethora of threats that compromise email inboxes.
Make the most out of the information in this article and create a strategy to fight cyber criminals who treat email communication as a potential way to cause harm.
You might be also interested in these blog posts:
- 6 Best Email Security Tools + Protection Services
- 5 Best Business Email Providers to Consider in 2023
Author bio
Laura Alexander is a freelance digital content manager and copywriter. She specializes in tech, ecommerce, and educational content.

