The Health Insurance Portability and Accountability Act, or HIPAA, was enacted by the United States government in 1996. It applies to any individual or company offering a service to a covered healthcare entity.
HIPAA protects the privacy of health information. Companies serving the healthcare industry, including data storage companies and email service providers, must follow HIPAA.
In this blog, we’ll share the basics of HIPAA-compliant emails and help you understand it better. So, let’s begin.
What is HIPAA-compliant Email?
Data security and privacy are always priorities in industries like healthcare. HIPAA was enacted to ensure these priorities are never ignored.
A HIPAA-compliant email must follow all the mandated rules while sending a patient’s PHI (Protected Health Information).
Here are the essential criteria for sending HIPAA-compliant email communications:
- Necessary safeguards should be implemented for ensuring the confidentiality and integrity of PHI;
- A business associate agreement should be signed with the email service provider;
- Your team members should be trained on email best practices to mitigate any risks of breach;
- Obtaining the recipient’s written consent before sending PHI by email is necessary in case of direct communication with the patient or beneficiary.
Before we examine these elements in depth, let’s quickly see when HIPAA compliance is required for email.
When is HIPAA Compliance Necessary for an Email?
HIPAA is a federal law that requires medical information to be kept safe and private while being shared. Therefore, any email containing protected health information or sent by a covered entity should follow HIPAA guidelines.
Violation of HIPAA regulations can attract severe criminal and civil penalties.
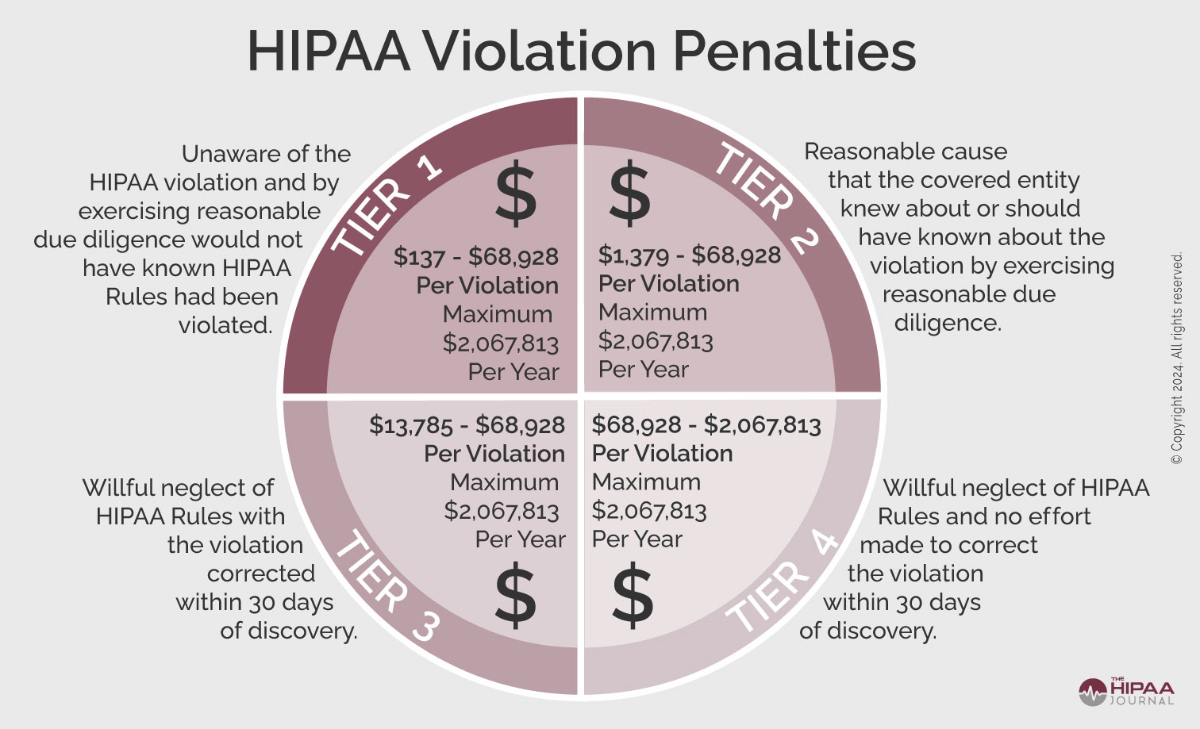
The violations are pretty severe and can dent the reputation and financial standing of any company. So, using a HIPAA-compliant email system is a must for companies that operate in the healthcare sector to send and receive secure messages.
But who should follow HIPAA regulations?
HIPAA rules mandate two types of entities to follow HIPAA regulations:
- Covered entities. Healthcare organizations, health insurance companies, healthcare clearing houses, or any health company directly dealing with patients;
- Business associates of covered entities. Companies providing services to the covered entities, like law firms, record storage companies, email service providers, etc.
So, basically, any email that contains protected health information (PHI) or is sent by a covered entity should be HIPAA compliant.
Not sure if HIPAA applies to you? Explore this checklist.
Key Elements of HIPAA-compliant Email
Email is one of the most common ways of communication between patients and providers. Companies collect, store, and transmit health information through this channel. So, every email must be compliant with HIPAA regulations.
Here are the most important elements of HIPAA compliance to keep the emails private and secure:
Regulatory Adherence
HIPAA compliance for emails requires all emails to be encrypted and follow certain set policies and procedures (more on this in the later sections).
Encrypting your email secures your email from unauthorized access during transmission.
HIPAA regulatory laws require emails to be encrypted under TLS 1.2 or 1.3 email encryption, which makes them unreadable, even if intercepted.
BAAs
BAA or a Business Associate Agreement is an essential element of HIPAA compliance for emails.
It’s an agreement between a HIPAA-covered entity like a hospital and a third party (business associate) who handles PHI on behalf of the covered entity. The third party can be an email provider, record keeper, law firm, etc.
The agreement covers the associate’s responsibilities for protecting PHI and ensuring secure transmission, storage, and reporting in case of a breach.
Here are the standard guidelines/elements of a business associate agreement:
- Permissible uses and disclosures related to PHI;
- Safeguard implementation guidelines for PHI protection;
- Reporting procedures for data breach or unauthorized disclosure;
- Return/deletion rules for PHI on contract termination;
- Procedures for auditing and monitoring compliance;
- A clause about third-party or subcontractor’s HIPAA compliance.
Policies and Procedures
Policies and procedures under HIPAA include the rules any covered entity must follow for compliance. These cover different scenarios to protect a patient’s health information.
Here are the three most important policies/rules under HIPAA compliance:
- HIPAA privacy rule. This involves procedures to protect a patient’s medical records from being released/used by non-covered entities. It covers all types of communication and prevents non-authorized access to PHI;
- HIPAA security rule. These rules cover how the health information should be protected. It includes putting administrative, physical, and technical safeguards for information integrity and transmission security;
- HIPAA breach notification rule. This involves procedures to notify affected parties, the US Department of Health & Human Services, and the media in case a security breach happens that affects more than 500 people.
Training
Training your staff is critical to complying with HIPAA norms for emails. Your contractors or staff will not figure out the complicated norms themselves.
Here’s what you can do to ensure proper training and effective compliance:
- Create a HIPAA email compliance plan and share it while onboarding a team member;
- Organize HIPAA training workshops for everyone who deals with PHI from time to time;
- Make them aware of possible human errors and breaches of the policies;
- Document email privacy best practices and information on how to use email encryption service.
Remember, when something changes, like staff member or your email service provider, mandatory refresher training is a must if you operate in the healthcare sector.
Audits and Monitoring
Only encrypting the email and training your team won’t make you HIPAA compliant. Regular audits and monitoring of access controls are also mandatory.
This involves implementing robust audit procedures. Here are some audit and monitoring rules:
- Implementing security measures such as two-factor authentication for restricting access to accounts that handle PHI;
- Maintaining audit controls for tracking and logging email activities;
- Monitoring unauthorized accesses or breaches in real-time.
Create professional emails in minutes — with Sender’s drag-and-drop builder email marketing becomes a breeze.
Usage of HIPAA Compliant Email
By now, you know that privacy and security are not just ‘good-to-haves’ when dealing with PHI. It’s a mandated responsibility.
Here’s a HIPAA compliant email checklist to ensure you’re on the right side:
1. Using Only HIPAA-Compliant Email Service with a BAA.
- Always use HIPAA-compliant email services for any communication involving PHI;
- Ensure that a Business Associate Agreement (BAA) is in place with the email service provider;
- Never use personal email accounts or a non-approved web portal/email service for work-related communications;
- If unsure whether an email service is HIPAA-compliant, consult with a legal expert.
2. Training on HIPAA Regulations and Secure Email Practices
- Organize mandatory HIPAA training sessions and workshops organized by the company periodically;
- Familiarize team members with the HIPAA Privacy Rule, Security Rule, and Breach Notification Rule;
- Use strong, unique passwords for your email account and enable two-factor authentication;
- Always verify the recipient’s email address before sending PHI;
- Log out of your email account when not in use, especially on shared or public computers;
- Never store personal information or PHI in personal computers or fill it in secure web forms (without approval).
3. Regular Risk Assessments and Audit Logs
- Establish risk assessment processes for every department;
- Log and monitor all email activities involving PHI;
- Regularly review your email practices to ensure they align with HIPAA requirements;
- Report any potential security breaches or unauthorized access to PHI immediately;
- Cooperate fully with any audit procedures or investigations related to email usage and PHI handling.
HIPAA-compliant Email FAQs
What are the criteria for HIPAA-compliant emails?
HIPAA-compliant emails must follow several guidelines to protect Protected Health Information (PHI). These include using a HIPAA compliant email provider with TLS 1.2 or 1.3 encryption for secure transmission.
Also, you must implement safeguards to maintain PHI confidentiality, and have a Business Associate Agreement (BAA) with HIPAA compliant email solution provider. Obtaining written consent from patients or plan members before sending them PHI via email, monitoring access controls, and maintaining detailed audit logs of email activities involving PHI are also mandatory.
These measures collectively ensure that any communication containing sensitive health information is sent via secure messages that are compliant with HIPAA regulations.
Is it against HIPAA regulations to transmit PHI via email?
It is not against HIPAA regulations to transmit PHI via encrypted emails, provided that proper safeguards are in place. To be HIPAA-compliant, emails containing PHI must be sent using HIPAA compliant email providers, and the sender must have authorization to share the information via an encrypted email.
Learn more about email marketing safety in this article: How to Send a Secure Email?
Disclaimer: HIPAA compliance is a legal matter. Any information in the article shouldn’t be considered legal advice. Please consult a legal expert to understand all the regulations and rules in depth.

